The Enhanced Mitigation Experience Toolkit 4.1 (EMET) is planned to assist in blocking hackers from getting entry to your system. Software loopholes and defects have become an essential component of life. Nearly all products has to go through with them and eventually, users are confronted with a queue of security updates. For users who are assaulted before the fresh updates have been deployed or who get compromised before an update is even usable, the outcomes can be very bad: malware, loss of PII, etc.
Security moderation technologies are planned to make it more tough for a hacker to exploit loopholes in a specific piece of software. EMET permits users to deal with these technologies on their system and offers many distinct advantages:
1. No source code required: Till now, most of the available mitigation (for example as Data Execution Prevention) have demanded for an application to be manually selected in and recompiled. EMET alters this by permitting a user to selecting in applications without compiling. This is particularly useful for deploying mitigation on software that was scripted before the moderation were available and when source code is not available.
2. Highly configurable: EMET offers a greater degree of coarseness by permitting mitigation to be singly deployed on a per process grounds. There is no requirement to enable a whole product or package of apps. This is useful in scenarios where a process is not in sync with a specific mitigation technology. When that occurs, a user can merely switch that mitigation off for that particular process.
3. Helps harden legacy applications: It’s not rare to have a hard dependence on old legacy apps that cannot be scripted again and demands to be discontinued slowly. Unluckily, this can easily impose a security threat as legacy application is infamous for possessing security loopholes. While the real solution to this is transmigrating away from the legacy application, EMET can assist manage the risk while this is happening by making it more tough to hackers to compromise the vulnerabilities in the legacy software.
4. Ease of use: The policy for all system wide mitigations can be seen and manually configured with EMET’s graphical user interface. There is no necessity to locate and decode registry keys or execute platform dependent tools. With EMET you can alter the setting with one uniform UI irrespective of the rudimentary platform.
5. Ease of deploy: EMET arrives in with built-in support for enterprise application and configuration technologies. This allows administrators to utilize Group Policy or System Center Configuration Manager to apply, configure and supervise EMET installations across the enterprise environment.
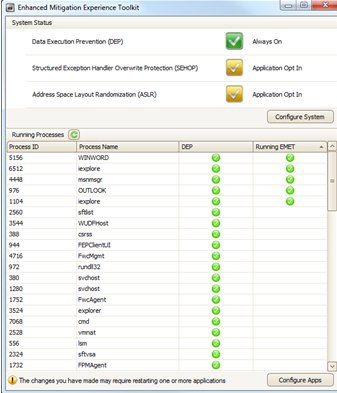
If you install EMET and do not “Configure System” the settings, it doesn’t perform anything to the Windows Data Execution Prevention (DEP) settings.
If you install EMET and “Configure System” settings to Recommended, it will alter the DEP to Turn on for essential Windows programs and services only, if you still have it set to everything.
If you install EMET and “Configure System” settings to Maximum, it will erase out the default DEP settings since EMET will be utilized in its place.




Post a Comment